Why the World’s Most Efficient Encryption is the First to Die
For decades, we’ve relied on the mathematical “walls” of Elliptic Curve Cryptography (ECC) and RSA to shield our most sensitive data. But those walls are about to be vaporized. While the industry has long viewed ECC as the gold standard for efficiency, that very efficiency has now become its greatest liability.
In the coming “Q-Day” – the moment a Cryptographically Relevant Quantum Computer (CRQC) goes online – the encryption protecting our financial systems, state secrets, and personal identities will shatter. And the first casualty won’t be your stored files; it will be every bit of data currently flying across the internet.
1. The ECC Trap: Why Smaller is More Vulnerable
In classical computing, ECC is superior to RSA. A 256-bit ECC key provides the same security as a 3072-bit RSA key, but with a significantly smaller computational footprint. However, in the quantum realm, smaller is easier to break.
The threat comes from Shor’s Algorithm, which can solve both the integer factorization problem (RSA) and the discrete logarithm problem (ECC) in polynomial time. Because ECC uses smaller keys to achieve its security, it requires significantly fewer logical qubits to crack.
- RSA-2048: Requires approximately 4,090 logical qubits to break.
- ECC-256: Requires only approximately 2,330 logical qubits to break.
Ironically, the efficiency that made ECC the darling of mobile devices and blockchain technology has turned it into the “low-hanging fruit” for quantum adversaries.
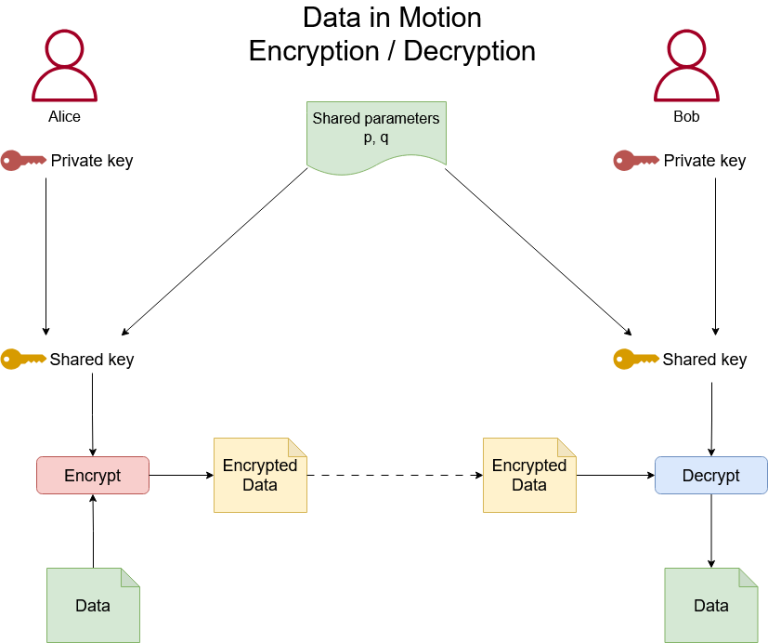
2. Data in Motion vs. Data at Rest: The Fragility of the Handshake
The most alarming aspect of the quantum threat is the distinction between data “at rest” (stored on a hard drive) and data “in motion” (moving through a network).
The Diffie-Hellman Achilles’ Heel
Data in motion is almost exclusively protected by the Diffie-Hellman (DH) or Elliptic Curve Diffie-Hellman (ECDH) key exchange. This protocol allows two parties to establish a shared secret over an untrusted wire.
In a quantum world, an attacker doesn’t need to break the actual AES-256 encryption used for the data stream. They only need to break the DH handshake that generated the keys. Once the handshake is cracked, the entire session is laid bare.
The "Harvest Now, Decrypt Later" (HNDL) Threat
This is why data in motion is uniquely vulnerable. Nation-state actors are currently intercepting and storing massive amounts of encrypted internet traffic – a strategy known as Harvest Now, Decrypt Later.
- Data at Rest: Often relies on symmetric keys or physical security. If you lose your disk today, it’s a problem today.
- Data in Motion: If your traffic is recorded today, it can be decrypted in five to ten years when quantum computers are powerful enough. Your secrets today have an expiration date you didn’t agree to.

3. The Alarming Qubit Timeline: 2026–2035
The window for action is closing faster than anticipated. Major players are no longer talking about “if,” but “when.”
Milestone
Expected Year
Capability / Impact
Quantum Advantage
2025–2026
QCs outperform classical computers in niche scientific tasks.
Error Correction Breakthroughs
2026–2028
Transition from “noisy” physical qubits to stable “logical” qubits.
ECC-256 Threshold
2030–2032
Quantum computers reach the ~2,500 logical qubit mark needed to break ECC.
Q-Day (RSA-2048 Broken)
2033–2035
The complete collapse of current public-key infrastructure (PKI).
By 2030, any data you send over the wire today using standard ECDH could be transparent to anyone with a high-end quantum processor.
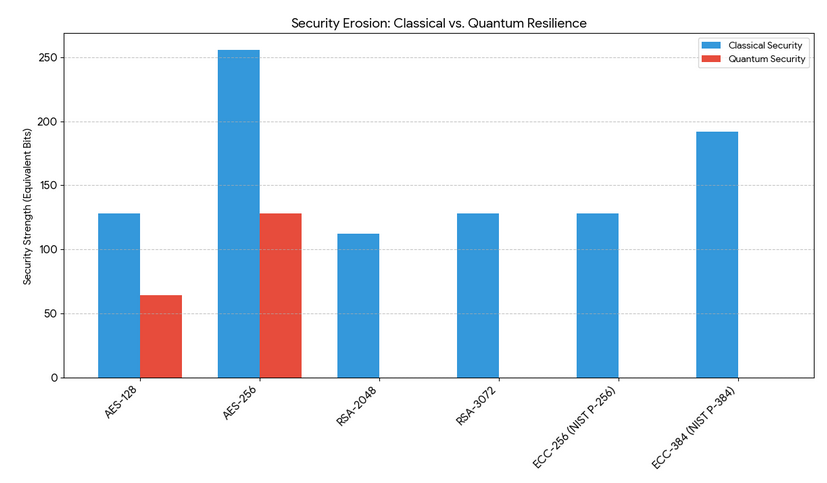
The data below illustrates the stark reality of the “Quantum Gap.” While symmetric encryption (AES) survives by having its security halved, asymmetric encryption (RSA and ECC) – the foundations of the modern internet – is effectively reduced to zero security by Shor’s Algorithm.
Algorithm
Classical Security (Bits)
Quantum Security (Bits)
Quantum Attack Method
Logical Qubits to Break
AES-128
128
64
Grover’s Algorithm
N/A (Symmetric)
AES-256
256
128
Grover’s Algorithm
N/A (Symmetric)
RSA-2048
112
~0
Shor’s Algorithm
~4,096
RSA-3072
128
~0
Shor’s Algorithm
~6,144
ECC-256
128
~0
Shor’s Algorithm
~2,330
ECC-384
192
~0
Shor’s Algorithm
~3,480
Key Takeaways from the Data:
- The ECC Vulnerability: Note that ECC-256 provides the same classical security as RSA-3072 (128 bits), yet it requires 62% fewer logical qubits to break (2,330 vs 6,144). This confirms that ECC is the “easier” target for a developing quantum computer.
- The Symmetric Shield: AES-256 remains exceptionally strong even in a quantum world, retaining 128 bits of security. This is why the primary threat is not the data encryption itself, but the Key Exchange (Diffie-Hellman) used to establish those AES keys.
- The “Cliff” Effect: As seen in the generated visualization, RSA and ECC don’t just get “weaker” – they experience a total collapse of security, whereas symmetric algorithms experience a manageable decline.
The Qubit Gap Analysis

The “gap” represents the dwindling time remaining before a quantum computer possesses enough stable logical qubits to perform Shor’s Algorithm on a scale that breaks modern public-key cryptography.
- The ECC-256 Threshold (~2030): As the graph indicates, Elliptic Curve Cryptography (ECC) is the first to fall. Because it relies on a smaller key size to provide its classical security, the mathematical structure is vulnerable to a quantum computer with approximately 2,330 logical qubits.
- The RSA-2048 Threshold (~2032): RSA, while requiring more qubits (approx. 4,096), follows closely behind. The time difference between the collapse of ECC and RSA is likely only 18 to 24 months.
- The Exponential Climb: While classical progress is linear, quantum development is following an exponential curve in error correction and logical qubit scaling.
Why this is Alarming for "Data in Motion"
Most “Data in Motion” (VPNs, HTTPS, Messaging) relies on ECDH (Elliptic Curve Diffie-Hellman). Looking at the graph, any data intercepted today and stored by an adversary will enter the “Vulnerability Zone” as early as 2030. This means the 10-year secrecy period required for many corporate and government communications is already being compromised by current traffic captures.
4. Why You Should Be Concerned Now
If your data has a “secrecy life” of more than five years—be it medical records, intellectual property, or classified communications – it is already at risk. The transition to Post-Quantum Cryptography (PQC) like ML-KEM (Kyber) must happen now, not when the first CRQC is announced.
The internet’s plumbing is built on Diffie-Hellman. Replacing that plumbing is a decade-long project, and we are already behind.
Cheers – Amit Tomar!!