TWO PAGERS
DESIGNS & ARCHITECTURES
LATEST ARTICLES
LangChain is a powerful framework for building applications powered by Large Language Models (LLMs). It simplifies the process of connecting LLMs with various data sources and tools...
Quantum teleportation is a real process in quantum physics that allows the state of a particle (like an electron or photon) to be transferred from one place to another — without physically...
In the last post, I explained about matrix operations, the eigen vectors, the operator matrix, etc. We also went through the basic single qubit gates, like the Pauli X gate, Hadamard...
My next few posts will be about quantum computing, (not the Iran’s version where they portrayed a ZedBoard Zynq-7000 as a quantum processor).We will code on IBM Qiskit libraries....
Speech-to-text technology converts spoken language into written text using automated speech recognition (ASR). It is widely used for applications such as voice assistants, transcription...
Model quantization is a technique used to optimize machine learning models by reducing their size and computational requirements, making them more efficient and suitable for deployment...
ESP32 is a single 2.4 GHz Wi-Fi-and-Bluetooth combo chip designed with the TSMC low-power 40 nm technology.
We will use the GPIO pins functionality only in this post, but each pin...
The physical design process is crucial in transforming chip designs into real-world products that drive our digital world. It involves a carefully planned series of steps aimed at optimizing...
A cryptocurrency is a digital currency designed to work as a medium of exchange through a computer network that is not reliant on any central authority, such as a government or bank,...
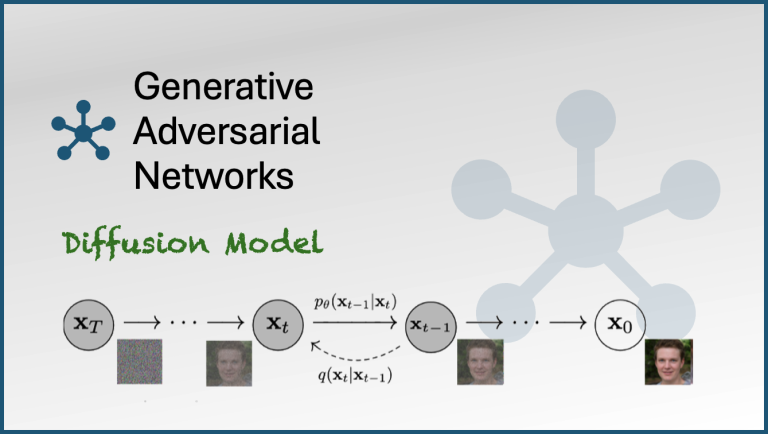
A generative adversarial network (GAN) is a class of machine learning frameworks and a prominent framework for approaching generative AI.The core idea of a GAN is based on the “indirect”...
When the transformer model came in the “Attention is all you need” paper, it changed the way NLP tasks were handled. I explained it in my previous post Transformer modelIn...
A neural network is a network of neurons. A neuron is a mathematical function which transforms the input data elements into a single output value.
In the above diagram the single...